Consulting Service Intervention
SECURITY LIFE CYCLE

Figure 1. Model – Plan, Do, Check, Act (PDCA)
GASTI suggests the development of the Information Security Master Plan (ISMP), structured into five phases:
-
Writing the Information Security Policy
Writing the Information Security Policy: defining the vision, the guiding principles and objectives for high-level security information organization. -
Inventory and Classification of Information Assets
Inventory and classification of information assets: This step allows for an inventory of all information assets of the organization and their categorization. It is conducted apart from the production of the ISMP, to which it serves as an input. -
State of Affairs
State of affairs: this step consists in identifying the risks and the relevant controls implemented by the organization to mitigate safety risks for each of the previously identified critical assets. -
Risk Analysis
Risk analysis: risk analysis is performed from a range of scenarios, representative of the reality of the organization and the state of the current. -
Security Master Plan
Security master plan: consignment of the preceding elements and writing of the action plan with respect to strategic and operational considerations.
Offered services
- Writing and reviewing the security policy
- Training
- Assisted prioritization of interventions
- Risk Identification
- Identification of controls in place
- Risk analysis
- Writing reports
Deliverables
- Security policy
- Safety Guidelines
- Safety Notices
- Training documents
- Blank forms and templates
- Overall inventory and categorization records
- Categorization matrix
- Categorized list of relevant controls
- Summary of evaluation of controls
- Status report of the current situation
- Risk scenarios worksheets
- Potential solutions
- Prioritization and action plan
- ISMP
In order to support organizations and comply with different requirements for protection and management of information, GASTI leverages its expertise and knowledge of governmental, private, and health & social services sectors to coordinate efforts of all stakeholders of the organization within an equipped methodology revolving around the following steps:
- Project planning and organization (schedule, activities, required committees).
- Presentation of and background on concepts and requirements.
- Adapting the intervention methodology to the context.
- Collecting and processing data with tools adapted to the context (different sizes, budgets, and HR, as well as different levels of progression in terms of safety management).
- Support in the completion of inventory, categorization and reporting of categorization of information assets.
GASTI suggests to subsequently carry out a situation analysis in an information security master plan (identification and analysis of risks and control measures).
Offered services
- Transfer of knowledge
- Project management
- Assisted collection
- Data analysis
- Preparing reports
- Support
Deliverables
- Raw data collection
- Data compilation
- Data analysis
- Asset categorization report
- Authority directory
Writing security architectures, taking into account the (4) processes with legal, human, organizational and technological dimensions
- Advise and support teams in the definition of objectives, issues and scope of their projects.
- Conduct preliminary and impact analyses, participate in the development of positioning and orientation.
- Guide security analysts and support project teams in the development phase.
- Participate in employee awareness and dissemination of standards, tools and approaches.
- Make recommendations for acquisition, system development or solutions and take responsibility for the development of some of them.
Development of a disaster recovery plan (DRP)
- Analyse risks and impacts.
- Risk Assessment.
- Identify critical information systems.
- Establish service continuity objectives.
- Define the technological recovery priorities.
- Inventory of assets and interrelationships.
- Identify roles and responsibilities.
- Determine resource requirements (human and financial).
- Identify supply solutions.
- Determine the actions to be implemented.
- Recovery strategies.
Development of a business continuity plan (BCP)
- List the activities and critical resources of a company.
- Identify risks that could affect these activities and their potential consequences.
- Implement strategies, possible answers and appropriate plans.
- Respond safely and effectively to incidents (minor or major).
- Exercise the ability to respond to incidents, keep updated strategies and plans and review them to ensure relevance.
Security Audit in accordance with the ISO 27002 standard
- Identify at risk IT processes in the organization.
- Schedule security audit mandates.
- Conduct security audit mandates.
- Use models, known repositories and tools.
- Present and explain the results of the audit.
- Act in accordance with ethical principles and rules of conduct of internal audit.
Social Engineering Test
-
Policies, procedures, and awareness.
The written rules that you develop to manage all areas of security, and the education program that you put in place to ensure that staff members know, understand and implement these rules. -
Physical security
The protections that manage all access to your site and your resources. For example, it is important to remember that if you place waste containers outside the company, they are outside of the physical security. -
Data
The company information, account details, email, etc. When you analyze the social engineering threats, you must include both hard and soft copies in your data security planning. -
Applications
The programs run by your users. You must explain how hackers can corrupt social engineering applications, such as email or instant messaging. -
Hosts
The servers and client computers used within your organization. Remember to protect users against direct attacks on these computers by defining strict guidelines on what software to use on business computers and how to manage security devices, such as user IDs and passwords. -
Internal network
The network through which your computer system communicates. This may be a local network, or wireless (WAN). The internal network has become less "internal" over the past years, as working from home and mobile phones has increased. Thus, you must ensure that users understand what they must do to work securely in all networked environments. -
Perimeter
The point of contact between your internal and external networks such as the Internet or your business partners’ networks, perhaps as part of an extranet. Social engineering attacks often attempt to breach the perimeter to launch attacks against your data, applications and to host your internal network.
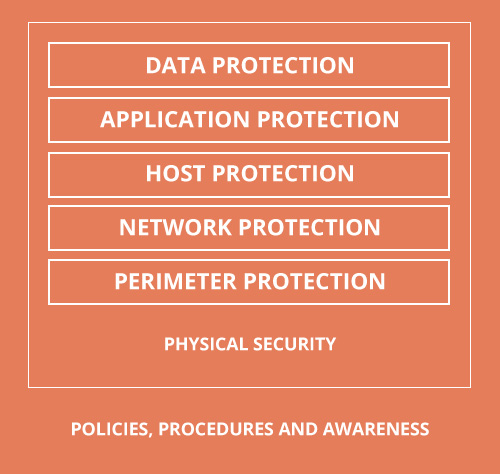
Figure 2. Security model for reinforced defense
When designing your defenses, the security model for reinforced defense allows you to visualize the areas of your business that are vulnerable to threats. This model is not specific to social engineering threats, but each layer must be protected.
The model’s main defenses are security policies, procedures and awareness. These defenses target the organization's staff, explaining what to do, when, why and by whom it should be done. The remaining layers can maximize your protection, but the main protection comes from a set of well-structured and well-defined rules that protect your IT environment.
GASTI can help you with this process.
Staff training on the sensitivity of information security
- Describe and understand the role of the user in maintaining information security.
- Identify policies to create a safe working environment.
- Identify remote users’ policies.
- Protect office equipment and mobile devices against threats.
